The Risks of ECDSA

Overview
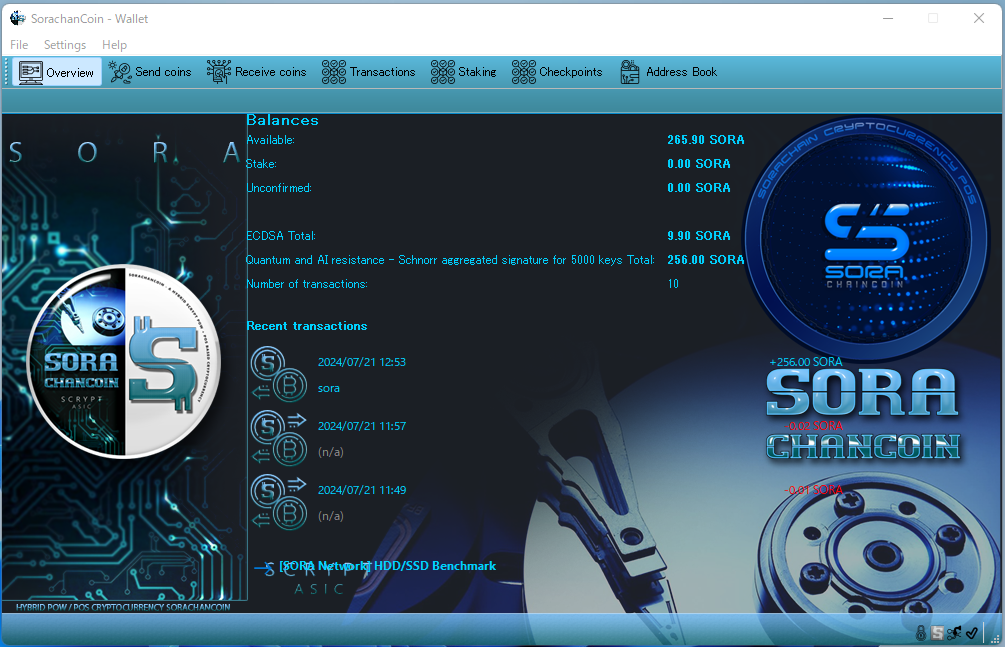
We have summarized information on quantum attacks against cryptography using elliptic curves (ECDSA).
Additionally, we have confirmed the operation of quantum resistance on Layer 1 (L1) with SORA. Therefore, we can confidently state that integrating quantum-resistant technology into a blockchain and making it operational is feasible, and there is no need to feel undue concern about quantum threats.
It is also worth noting that RSA and ECDSA have "completely different structures," and blockchain utilizes ECDSA. Discussions around quantum computers often highlight vulnerabilities in RSA, particularly regarding factorization. However, even if factorization becomes feasible, ECDSA will not be compromised. RSA has a relatively simple structure, while ECDSA employs elliptic curves, making its computations significantly more complex. Notably, the calculations and structural properties of elliptic curves require extensive resources for quantum computers to efficiently solve, making it far more challenging to break ECDSA compared to RSA at this time.
Please find the relevant links below.
secp256k1:
The risks of secp256k1
Schnorr Signatures:
The risks of Schnorr Signatures
Ed25519:
The risks of Ed25519